I have recently come across this intriguing report – “NSA: We ‘don’t know when or even if’ a quantum computer will ever be able to break today’s public-key encryption”
Its conclusion was “In a world where users will divulge their passwords in return for chocolate or in response to an enticing phishing email, the risk of quantum computers might not be our biggest threat.”
Let us assume, however, that quantum computing has suddenly made a quantum leap and becomes able to break today’s public key schemes. Would we have to despair?
We do not need to panic. Bad guys, who have a quantum computer at hand, would still have to break the part of user authentication, that is NOT dependent on the public-key scheme, prior to accessing the target data, in the normal environment where secret credentials (= remembered passwords) play a big role.

What is remembered in human brain is outside the realm of computers. Quite a few cryptography-obsessed security people are often indifferent to this simple and plain observation.
We could look to the power of identity assurance by our own volition and memory. It could help force quantum computing to work just for benefiting people, not for hurting people.
As such, whether quantum computing makes quick progress as anticipated or not, the solid digital identity with secret credentials will remain critical
What if the password is removed from digital identity?
A different observation could be extracted from the same report; “What does not exist will not get abused. We would achieve a more secure world by dumping the password altogether”. Some people seem to have jumped on this seemingly alluring perception. However, its consequence would only be catastrophic.
Assume that someone mentions “The army is so vulnerable to air attack. What is vulnerable to attack is detrimental to our defence. Therefore, we must remove the army so that we will have a stronger national defence.”
You might well suspect that they are making a bad joke because this proposition sounds too insane. It is not the case, however. The army-less defence should be viewed as valid where people believe in the merit of ‘password-less authentication.
“The password is so vulnerable to abuse. What is vulnerable to abuse is detrimental to security. Therefore, we need to remove the password so that we will have stronger identity security.” Here, the army is to national defence what the password is to identity security.
Practically, where our identity can be established while we are asleep, we would no longer have a restful sleep unless staying alone in a closed space locked from within or fenced by faithful bodyguards.
There is more to it. Where our identity is established without our volition/will confirmed, democracy is fatally eroded.

We do wish that no democratic governments will be misguided to get trapped in this kind of false reasoning.
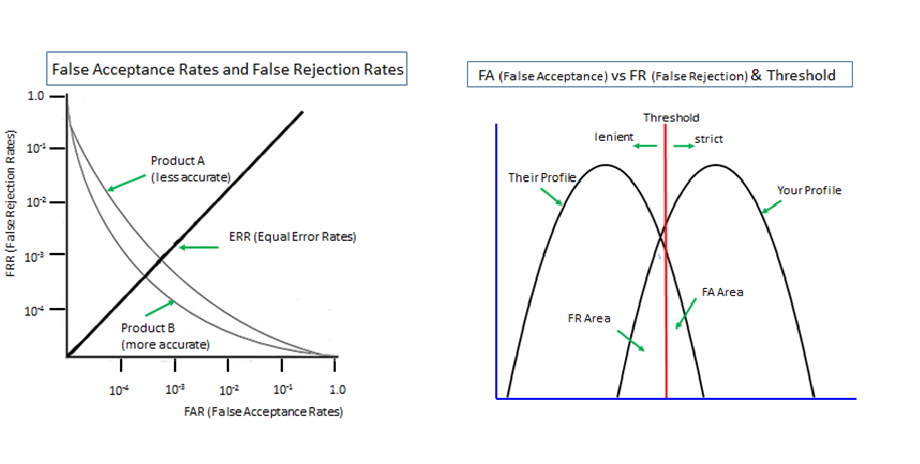
By the way, many people consider biometrics as a key component for passwordless schemes. Our view of probabilistic biometrics is summarised in this article “What these 2 graphs tell us about biometrics”
Dual Causes of Password Predicament
Now we are going to examine the issues of secret credentials.
Our password headache may well be the consequence of these dual causes – ‘Use of Impracticable Password’ and ‘Non-Use of Practicable Password’; Everyone grumbles at the former, while few are well awake to the latter.
The practicable password we mean is the one that accepts ‘Non-text credentials’ in addition to ‘Textual credentials.
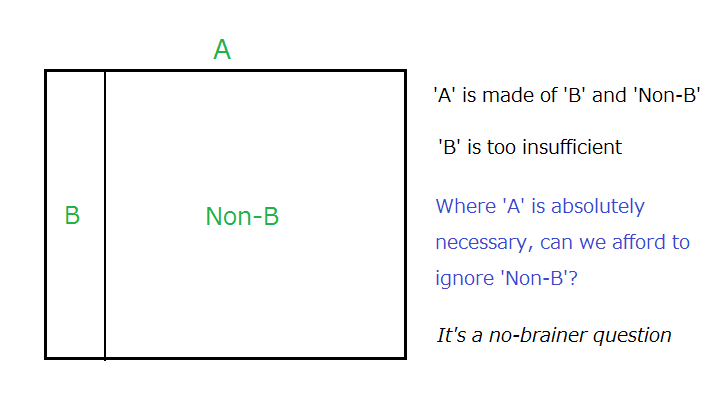
The secret credential (A) is made of the text credential (B) and the non-text credential (Non-B). The relationship between the three elements is illustrated above.
It is really a no-brainer question unless we are so reckless as to assume that a safe and orderly societal life can exist without a solid identity assurance that can only be made possible by the solid secret credential.
Episodic Image Memory
As the non-text credential, we propose to make use of our pleasant episodic image memory that had been acquired years or decades ago and solidly inscribed deep in our brain.
Images of toys, dolls, dogs, and cats, for example, that our children used to love for years would jump into our eye even when we are placed under heavy pressure and caught in severe panic, meeting any need of identity assurance in any demanding situations.

Use cases are quoted in this introductory 90-second video “Digital Identity for Global Citizens”
The aim of our enterprise is to make Expanded Password System solutions readily available to all the global citizens: rich and poor, young and old, healthy and disabled, literate and illiterate, in peace and in disaster – over many generations until humans invent something other than ‘digital identity’ for safe and orderly societal life.
Bring a healthy second life to legacy password systems
We do not have to replace or rebuild the existing text password systems for making use of episodic memory; images of our episodic memory can be turned into a high-entropy code with a simple tweak.
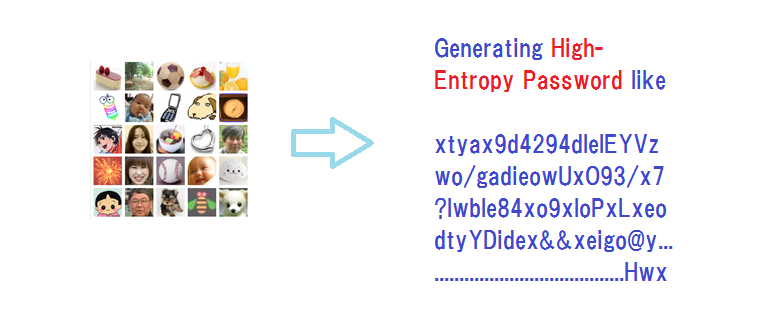
All that we need to do is ensure that existing password systems accept very long passwords, desirably hundreds of characters, for obtaining very high-entropy hashed values that can stand fierce brute force attacks.
The logic of ‘image-to-code’ conversion is demonstrated on our website along with relevant writings. Everyone can freely try and experience the flow of the process here – https://www.mnemonicidentitysolutions.com/
Password Manager powered by Expanded Password System
“Expanded Password System is no bad, but we do not need it. We can rely on password managers that are protected by a single strong password. Password predicament is already sorted out by password managers”. This is what we often hear here and there.
Then, what if we come up with a password manager powered by an Expanded Password System?
It is ‘leak-proof’; the passwords, which are generated and regenerated on the fly by our image-to-code converter from users’ hard-to-forget episodic image memory, will be deleted from the software along with the intermediate data when it is shut down.
The merits of episodic image memory enable us to easily handle multiple password managing modules with multiple unique sets of images; it helps us avoid creating a single point of failure.
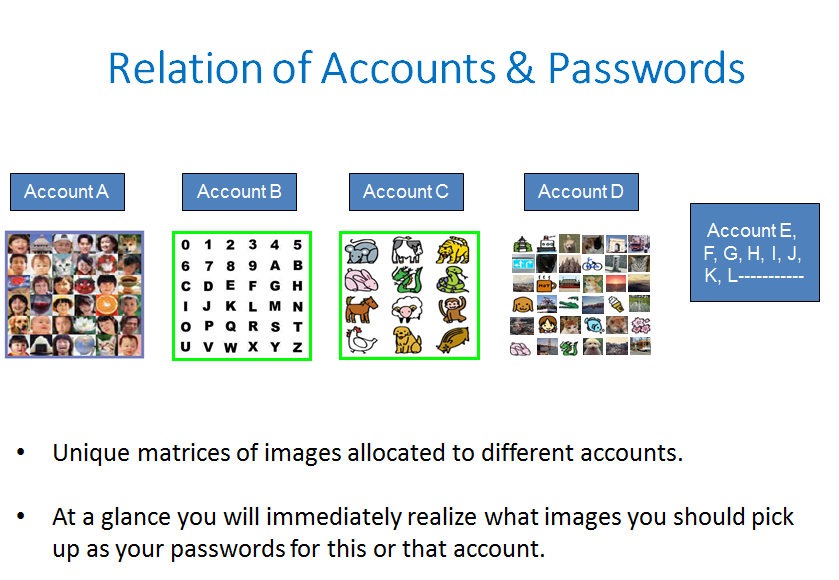
We expect the EPS-powered password manager to be a good tool to actually bring a healthy second life to ubiquitous legacy password systems.
Expanded Password systems will continue to contribute to safe cyberspace even when quantum computing has destroyed the part of identity authentication that depends on public-key schemes.
Please keep an eye on the progress.








